Attack Landscape of 2018, So Far
2017 had WannaCry, NotPetya, and an explosion of activity on our global network of honeypots. 2018 in comparison has been, well, a little quieter.
For the last two years, we’ve been reporting traffic seen on our honeypot network. These honeypots, or decoy servers that are set up to attract the interest of attackers, provide an interesting high level look at attack patterns and trends in cyberspace. Today we release our report, Attack Landscape H1 2018, on honeypot activity from the first half of the year, as well as the malware and social engineering trends we’ve seen so far in 2018.
Reports like these typically mention that malware and attacks have increased or even multiplied due to the progressively greater sophistication and commoditization of the cybercrime world. But this time, surprisingly, we noticed a slowdown in attacks as compared to previous periods.
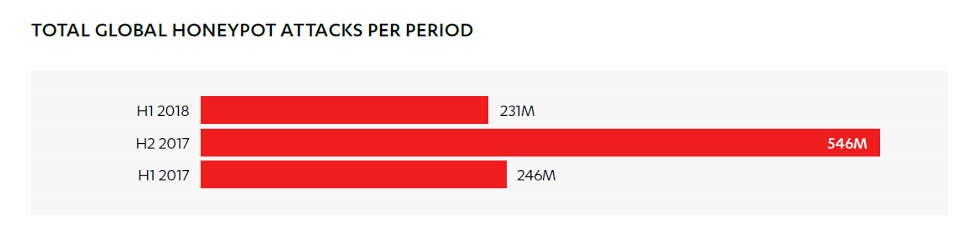
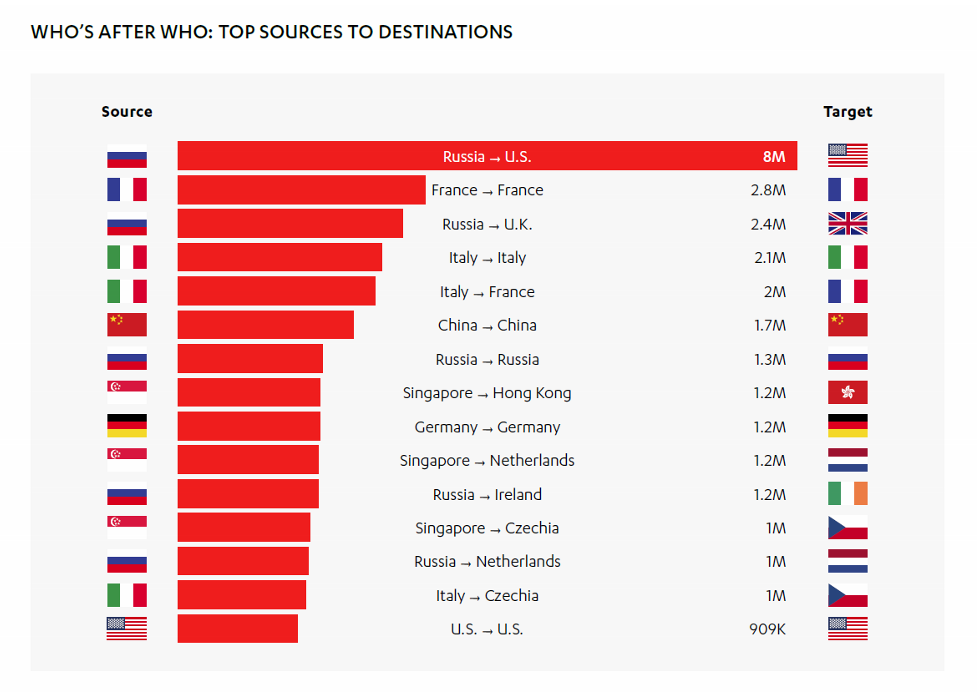
One big factor in this slowdown is a dropoff in traffic from Russia, who usually takes the top spot as greatest attack source but who slipped to number two this period. Russia’s 32.7 million probes to our honeypots this period are just a fraction of its activity in previous periods – 108 million in the first half of 2017, and 146 million in the second half.

One thing that didn’t change is the top adversarial relationship between countries: Russia targeting the US. The volume of attacks from Russia to the US is also much lower than before – only eight million in H1 2018, as compared with about 140 million for all of 2017.
In other news, our report documents the slowdown of ransomware and the new threats that have popped up in its place. Ransomware, while still a threat to take seriously, has been overtaken in numbers by the trend of cryptojacking – unauthorized borrowing of a device’s computing resources for cryptocurrency mining.

As we reported recently, spam has also resurged in prominence, coming in at #1 as an attack vector. This is an indicator that cyber criminals are running out of other attack vectors due to improved system security against software vulnerabilities and exploits. Left without ways of exploiting technology, attackers are attempting to exploit users through social engineering instead. Their attempts, it seems, are not futile – according to data from MWR Infosecurity’s phishing assessment platform, click rates have risen from 13.4% in H2 2017 to 14.2% in 2018. Our data on spam click rates by industry shows which sectors are most vulnerable to falling for spam:

For much more, including the ports and protocols that received the most attention from attackers this period, a closer look at aggressive periods from select countries, our system of detecting attackers within the customer environment, and more on the malware and social engineering trends of the period, download our full report, Attack Landscape H1 2018.
DOWNLOAD REPORTFor a snapshot of major trends of the period, download our infographic, Threat Landscape Snapshot H1 2018.
DOWNLOAD INFOGRAPHICCategories