EPP and EDR – What is Their Role in Your Cyber Security?
Although endpoint security technologies are converging, they can still be roughly divided into two categories: endpoint protection platforms (EPP) and endpoint detection and response solutions (EDR).
The delineation between the two is quite clear to most IT security professionals. Simply put, EPP is preventive security – EDR provides detection and response capabilities. Overall, it’s a good idea for most businesses to use both EPP and EDR to ensure that they’re prepared for today’s attacks.
However, there’s often confusion about these solutions’ specific roles in building modern cyber security strategies. Should you prioritize EPP over EDR or vice versa? What capabilities should you seek in each solution? What’s the best way to stop advanced attacks? What kind of tooling do you need for incident response?
Let’s go through some basics in an attempt to shed light on these questions.
EPP prevents the most common cyber attacks
At its core, EPP is all about attack prevention, especially when it comes to so-called commodity threats: bulk malware, non-targeted phishing and basic online scams.
This is the white noise that permeates the threat landscape. Most IT security teams can deal with these threats effectively enough, as long as they have access to solid tools.
Although they’re quite well-understood, commodity threats are still a priority for many companies. This is due to their high volumes and capacity to disrupt operations. Widespread ransomware infections, for example, can bring your business to a grinding halt. Similarly, you don’t want to bog down your IT department with constant requests for malware removal or full device remediation for work laptops.

In addition to blocking traditional threats, EPP can also protect you from more advanced attacks. Good preventive security forces hackers to work harder, which tends to increase cost structures. This will most likely cause opportunistic aggressors to abandon you as a target and move on to easier prey. EPP can also smooth out your detection and response processes by reducing alerts, which lowers your IT security team’s workload.
Even though we’re talking about endpoint protection here, it’s important to note that the endpoint itself doesn’t cover everything. To maximize your capacity to both prevent threats and collect data for forensic purposes, you probably need a good network protection suite that integrates with your EPP. Security incidents get much more difficult to handle when you don’t have data – or can’t correlate it – from these two sources effectively.
Keeping all this in mind, here are some basic capabilities you should seek out in your EPP when it comes to prevention and incident response:
- Proven malware detection rates by 3rd party evaluators like AV-TEST
- Prevention of common exploits, including ransomware
- Detection and prevention of code injection
- Integration with a host-based firewall
- Content inspection of browser data
- Application whitelisting with adjustable configuration
Based on its good cost-benefit ratio, EPP is often prioritized in many companies over other security solutions. And there’s nothing wrong with this, as long as it’s a conscious decision based on threat modelling and risk assessments. But if you find yourself relying on EPP simply because it has worked in the past, it’s time to have a closer look at your security strategy.
EDR detects attacks that have bypassed your EPP
Endpoint protection platforms are invaluable in terms of threat prevention, but they are not designed for post-compromise security. Essentially, if an attack bypasses your firewall and EPP, you will be unable to detect it without additional tooling.
This is where endpoint detection and response comes in. The basic idea behind EDR is to empower your IT security teams to identify malicious activity among normal user behavior. This is achieved by collecting behavioral data and sending it to a central database for analysis. Using AI-driven analytics tools, EDR solutions are able to identify patterns and detect anomalies. These can then be submitted for further investigation or remediation.
EDR is increasingly valuable in the modern threat landscape, as companies are encountering more and more targeted attacks that cannot be stopped with traditional security measures. The game has changed for good. It’s no more about building walls around your assets – rather, you need to install sensors that can detect intruders when they inevitably find ways to bypass your security.
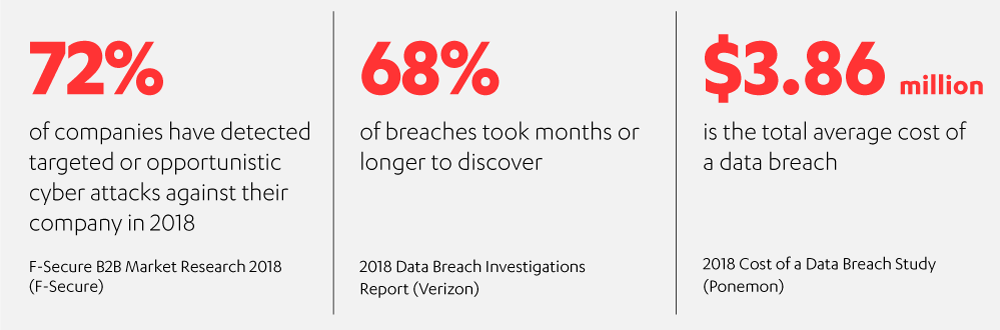
Here are some basic capabilities to look for in an EDR solution – combining both threat detection and incident response:
- Detecting potentially malicious behavior, like registry key editing and process launches
- Placing detections into a context and visually presenting the attack with all impacted hosts
- Including threat intelligence about the prevailing threat landscape
- Providing guidance on how to respond, instead of just showing low-level event information
- Allowing the remote stopping of attacks by isolating all impacted hosts from the network
EDR is a solid way to enhance your security in terms of detection and response. It’s not a silver bullet, however – you still need someone to run it properly and act on the alerts it produces.
Operators that understand the context of different threats, have knowledge of basic attack methodologies and possess the ability to respond to threats are not easy to come by. In fact, many industry analysts are predicting a large shortage of capable talent in the near future.
This requires you to make realistic evaluations into your current capabilities. Do you have a dedicated IT security team? If not, do you need to hire more people or look into outsourced services? Do they have the skills to utilize EDR to the fullest extent? Can they respond to incidents, either with the capabilities provided by EDR or other tools?
Automation and outsourced support can be huge assets in addressing these types of competence problems. F-Secure’s EDR solution has been designed with this in mind, providing you both with automated response actions and the capacity to escalate difficult cases straight to our experts.
The bottom line with EPP and EDR?
In short, most organizations would do well to look into both EPP and EDR to build a sufficient security posture against modern cyber attacks. One can be prioritized over the other depending on your company’s specific needs, but both effective prevention and response are needed in the modern threat landscape.
Which is more important for your company: a higher likelihood to stop attacks at the endpoint or detect them quickly once they’re past your preventive defenses? Ultimately, this is a question for top leadership, and the answer should reflect your industry, network structure, organizational culture and security team’s capabilities.
Categories
