Phishing is here to stay
Phishing is an online threat that doesn’t seem to go away, in particular, because it has been very effective. Our H1 2020 Attack Landscape report has indicated that email still remains the preferred method for malicious threat actors for delivering spam, phishing and other malicious content.
The current pandemic that is going on in the real world has not changed or slowed down the pace of malicious threat activities in the cyber world. Phishing emails remain rampant, and with most organization infrastructures shifting to cloud and with the proliferation of remote work and studies, the phishing themes have also shifted to target credentials of those tools and platforms.
In this post, we review the statistics of the phishing emails we have seen since October 2020.
Web and application hosting services a popular choice
The top 3 domains seen hosting phishing pages come from web or application hosting services while the rest are mostly compromised domains.

Figure 1: Breakdown of the top 20 domains seen hosting phishing pages
These hosting services have recently become a popular choice for the attackers because the cost involved in setting up a webpage is relatively low or sometimes even free for basic use. As phishing pages are oftentimes taken down quite quickly after being reported, the use of hosting services enables threat actors to generate and switch their pages rapidly without substantial downtime.
By placing phishing pages to hosting services, threat actors also try to add a layer of legitimacy for the users as those services provide SSL certificates (reflected in the “https” prefix in the URLs). We expect this to remain as a popular choice for threat actors because it saves their resources and efforts of identifying domains or web servers that they could compromise before hosting their phishing pages.
Microsoft O365 credentials increased in popularity
As indicated in our H1 2020 Attack Landscape report, Facebook remains the most frequently spoofed brand in phishing emails. Webmail and cloud application providers have been inching up the popularity list in the recent months. That said, spoofed financial institution emails still make a bulk of what we have seen, as reflected in the sector breakdown table below.
| Facebook, Inc. | 23% |
| Outlook | 11% |
| Office365 | 9% |
| Russian Post | 9% |
| Halifax Bank of Scotland Plc | 8% |
| Lloyds TSB Group | 4% |
| Amazon.com Inc. | 4% |
| PayPal Inc. | 4% |
| 4% | |
| Chase Personal Banking | 4% |
| Webmail Providers | 3% |
| RuneScape | 3% |
| Bank of America | 2% |
| LinkedIn Corporation | 2% |
| Orange | 2% |
| Netflix Inc. | 2% |
| DHL Airways, Inc. | 2% |
| eBay Inc. | 2% |
| Microsoft OneDrive | 2% |
| Apple Inc. | 2% |
Table 1: Top 20 brands spoofed in phishing email
| Financial | 29% |
| Social Networking | 20% |
| Online/Cloud Service | 15% |
| Email Provider | 9% |
| Logistics & Couriers | 8% |
| Telecommunications | 6% |
| e-Commerce | 5% |
| Payment Service | 4% |
| Gaming | 2% |
| Government | 2% |
Table 2: Breakdown of the sectors used as phishing email themes
Microsoft O365 credentials are a popular target as organization are intensifying their migration to cloud applications to better support remote workers.

Figure 2: Example of Microsoft O365 phishing email

Figure 3: Fake Microsoft O365 password expiry email
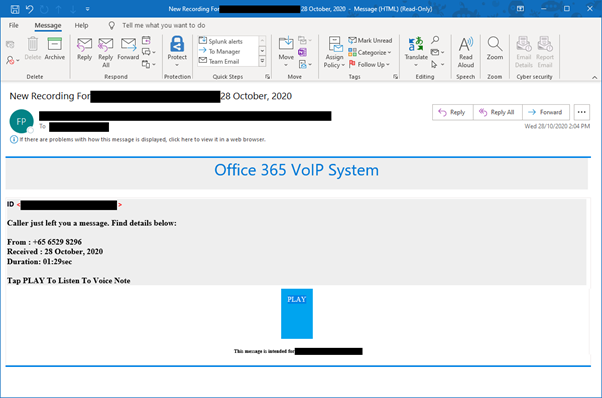
Figure 4: Fake Microsoft O365 VoIP system email
Financial themed phishing emails continue to be used
While cloud application credentials may be useful for threat actors to gain initial access to an organization, financial institution credentials remain a lucrative target for monetary gains amidst the pandemic. The pie chart below drills down specifically to the top 20 financial institutions which have often been spoofed in the past few months.

Figure 5: Breakdown of the top 20 financial institution themed phishing emails
Collaborative tools are not spared
With the recent shift to remote work in many organizations, there has been a noticeable growth in adopting collaborative tools for daily work. Video conferencing and online document collaborative tools are common now for remote workers, as a result of the pandemic.
Threat actors have been known to be quick in adapting to changes in their tactics, and the COVID-19 pandemic is no exception. We have spotted a number of emails attempting to phish credentials for various collaborative tools.

Figure 6: Phishing email disguised as DocuSign document review

Figure 7: Phishing email disguised as Microsoft Teams message

Figure 8: Fake email phishing for Zoom video conferencing credential
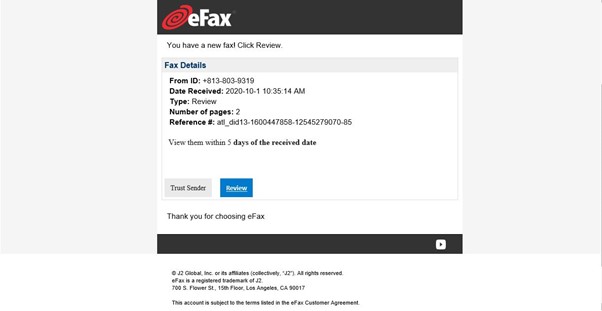
Figure 9: Phishing email disguised as eFax online fax service
Where do we go from here
As threat actors continuously update their tactics and techniques, it is also up to us all to collectively update our defense approaches. Email will probably remain as a prevalent vector to phish for credentials or even to deploy malware. Human intelligence is then the most effective protection against phishing attacks.
Although many of us have seen best practices suggested for thwarting phishing attempts, there is no harm in repeating them again here:
- If you are requested to login to a service through email, it is always better for you to manually type in the URL of the service instead of clicking on the link provided in the email.
- If there is a need to click on the link, always hover your mouse to verify the URL before clicking it.
- HTTPS sites are no longer a good indicator of a safe site. Always verify the URL that you are visiting.
- Use a URL expander service to identify the final landing page of shortened URLs.
- Watch for email senders that use suspicious or misleading domain names.
- Don’t click on links or attachments from senders that you don’t recognize. More so, don’t open any attachments that you are not expecting to receive. If you know the sender, call up or send a new separate email to them to verify the authenticity of the initial email.
- Enable and configure two factor authentication (2FA) in online services whenever possible.
- Use a unique password for each application or website. If you fell for a phishing attack, change your password immediately.
- Never provide sensitive information (username, password or personal information) over email. A legitimate website or service will never request such information over email.
Research activities
Protecting organizations and people from phishing threats is one of the key topics in SAPPAN – an ongoing Horizon 2020 project (https://sappan-project.eu/, received funding from the European Union’s Horizon 2020 Research and Innovation Programme Under Grant Agreement no. 833418), where F-Secure is a partner. In the first phase of the project, a number of Machine Learning-based classifiers were built for identifying phishing URLs and public-key certificates used by phishing domains. Extensive validation of the classifiers as a part of the overall F-Secure’s phishing detection logic, planned in the next phase, will provide evidence of their suitability for several applications in cyber security.
Categories