So Many Vulnerabilities, So Little Time
There’s way too much hype about zero day vulnerabilities. The website CVE Details shows an average vulnerability score of 6.8, across all known vulnerabilities, on all known platforms. Of the over 80,000 known vulnerabilities in their database, 12,000 (almost 15%) of them are classified as high-severity. Remember, though, that these vulnerabilities exist over plenty of different client and server-side applications (including, you guessed it, Adobe Flash).
From a company’s point of view, handling high-severity vulnerabilities is a number one priority. And they get handled in well run organizations. High-severity vulnerabilities get a lot of visibility, and because of this, they’re patched on the spot. But vulnerabilities alone don’t make up your company’s entire attack surface. Your CISO is probably more worried about phishing and upstream attacks than internal network misconfigurations and unpatched internal systems.
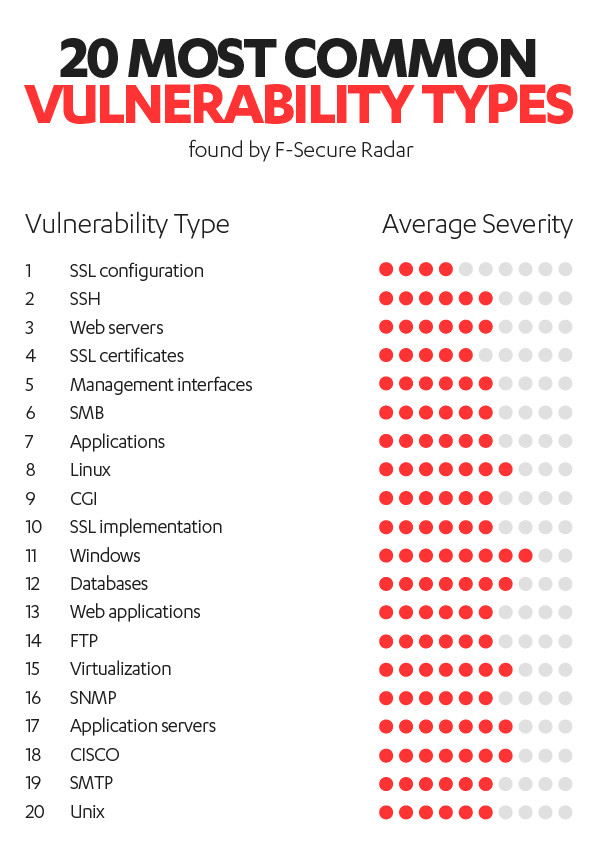
As an IT admin, taking care of infrastructure is your biggest concern. Of course, you’re going to perform triage when a new high-severity vulnerability surfaces. But what about the rest of them? Applying every patch to every piece of software on every system on your network, as the patch is released, is just not feasible. That’s why admins rely on periodic patch cycles to fix low severity vulnerabilities, if they do at all.
Taking time out of their day to understand the implications of every newfound vulnerability out there is too much ask for most IT admins. So, in many cases they simply don’t bother. When looking to apply patches, admins often ask questions such as:
- How exposed is the system?
- Will this patch break something else?
- Do I even know what this vulnerability means?
Using our Radar vulnerability management service to analyze vulnerability trends within our customer base shows exactly this:
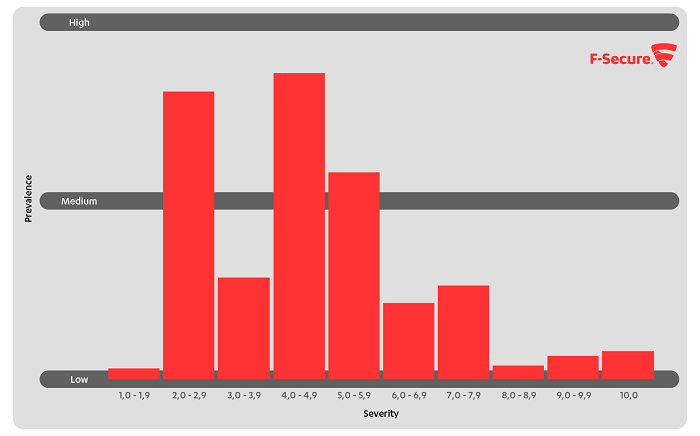
High severity vulnerabilities were rare to non-existent. The vast majority of unpatched vulnerabilities we found were of low-medium severity. Of these, it’s interesting to note that TLS/SSL and OpenSSH misconfigurations were common. Remember, though, that although they’re labeled misconfigurations, it’s possible these systems were configured that way in order to interoperate with customer, partner, or proprietary in-house services.
Our Information Security Manager, a member of our CISO office, looked at the graph and concluded that if this represented the situation at our own company, he’d be able to sleep at night.
Here are Andy and Sean from our Tech Outreach Office, with more on this.
This article was adapted from our recent report, The State of Cyber Security 2017. Read more about cyber security trends and topics when you download the full report here.
Categories
