The anatomy of a modern cyber-attack
To successfully defend your organization against cyber-attacks, you need to think like the attacker. But what does that really mean? In short, it is about two things: understanding what attackers need and how to deny them access to those resources.
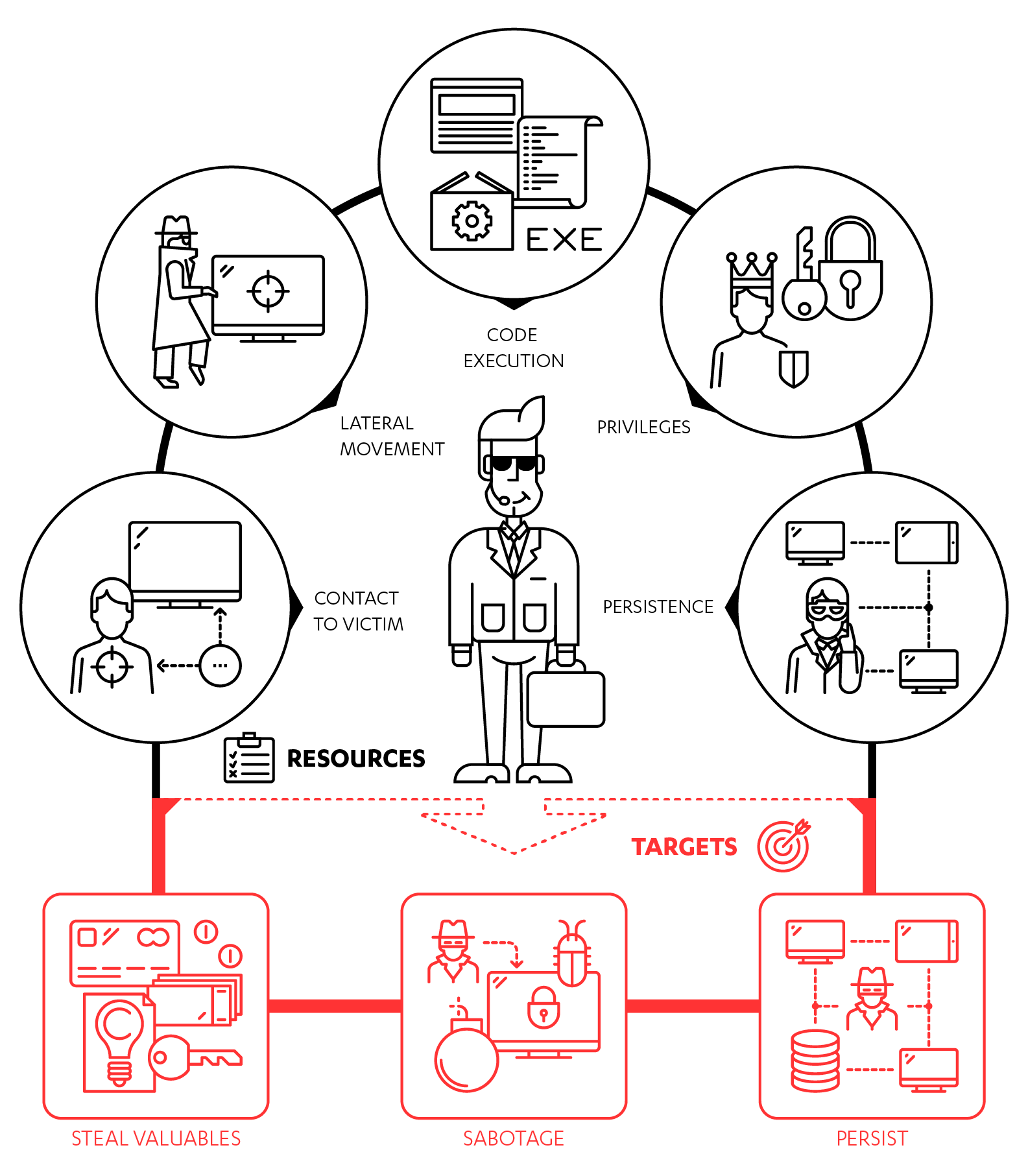
What is the target of the cyber-attack, and what does it need?
One of the most typical ways to contact the victim is by email. The scam emails of today look really convincing – they are a far cry from the clumsy attempts of a few years ago. Using personnel or organization recon, the attacker will know the details of the victim and use those details to make the attack email seem extremely credible.
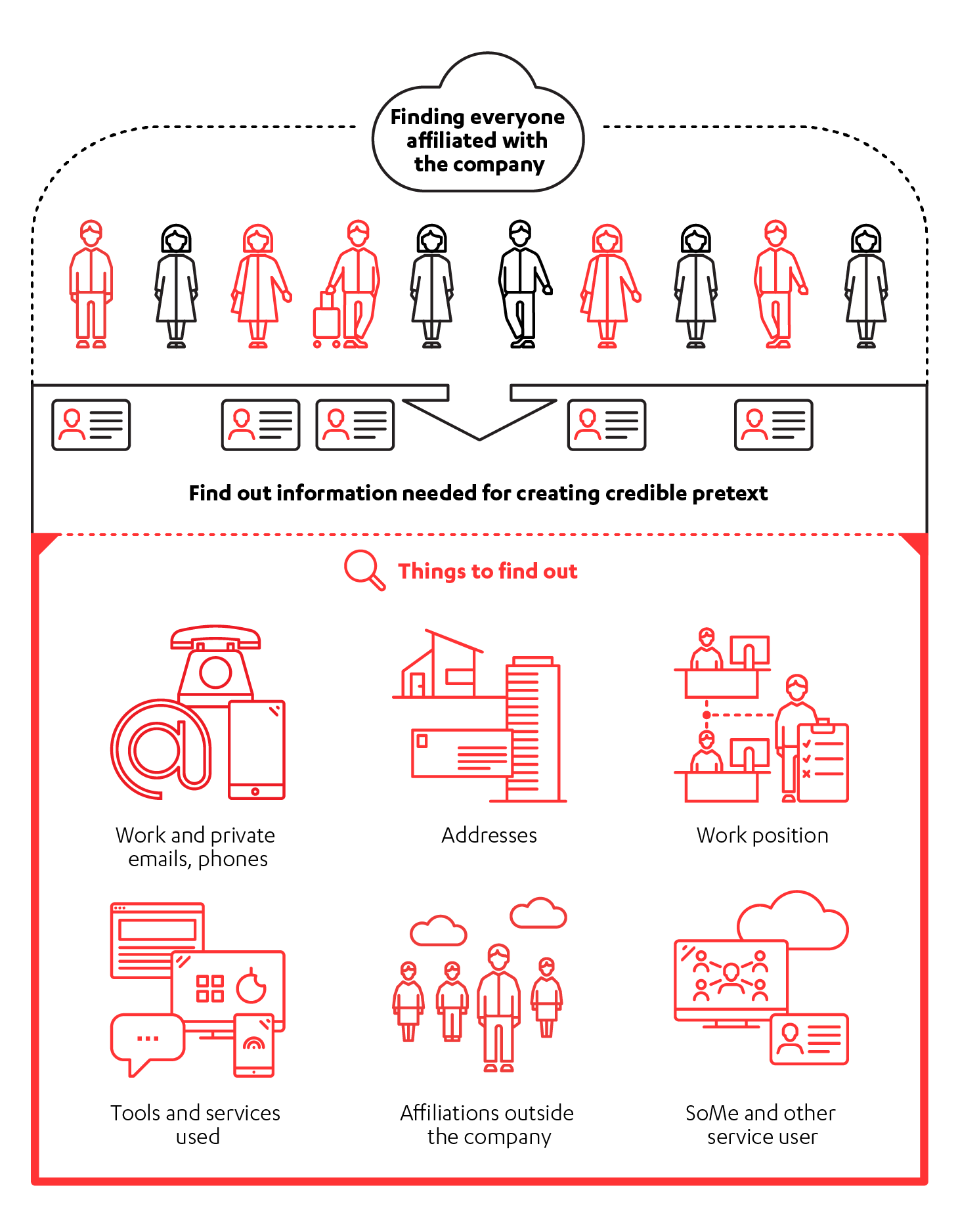
So how does the attack proceed after contact?
The original document that the victim receives contains the attack that takes over the document reader with the same access as the user. Then the attack continues:
- Drop a payload EXE to some location and execute it
- This crashes the exploited Word, Acrobat, etc process
- The dropped payload drops a clean document
- The clean document is loaded to give the user the expected document
- The payload is now free to continue in the background
- Usually the next action is to connect to C&C, or wait for a trigger
Email-based attacks are not the full picture though…
While email might be the most utilized channel to connect to victims, there are also several other ways to compromise them.
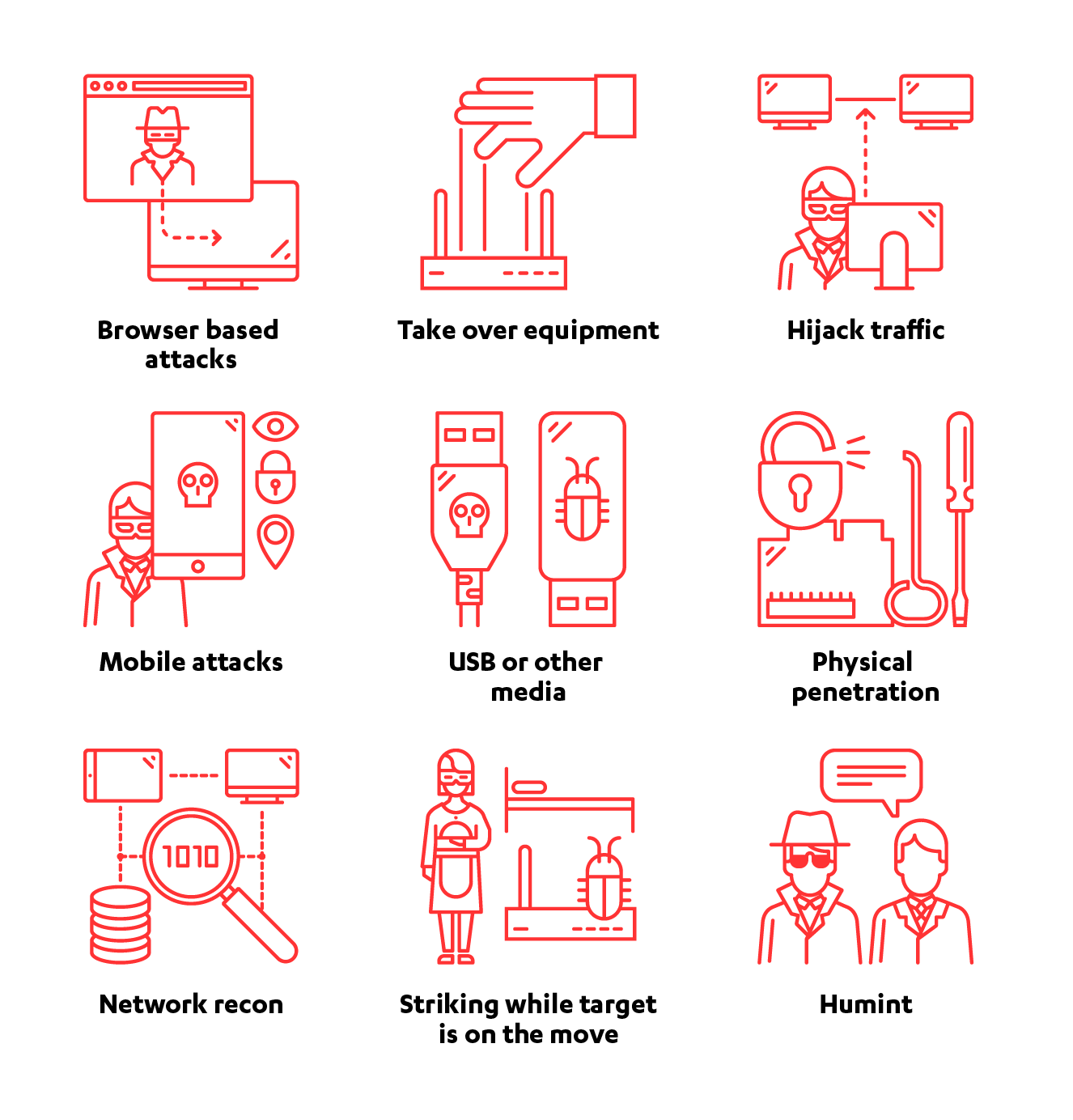
So how do you protect yourself and your organization against recon and penetration?
Jarno Niemelä from F-Secure Labs gives the following advice for any organization that wishes to minimize the risk of a successful cyber-attack:
- Recon yourself and use this as training and hardening material
- Train your people to resist social engineering and HUMINT
- Harden your internal network to resist and spot recon activity
- Improve your physical security, make the office difficult to penetrate
- Protect equipment, especially mobile equipment
Categories
