The State of Cyber Security 2017
2016 was a remarkable year for info security. There were allegations of US election hacking, IoT botnets, SWIFT banking heists, Yahoo breach disclosures to the tune of 1.5 billion passwords, and rampant ransomware incidents. With every story playing out in the media, there were lessons organizations could learn and apply to their own cyber security strategies to avoid becoming the next victim.
Researchers at F-Secure saw their share of incidents, malware, vulnerabilities, and hacking last year, and they’ve got experiences and learnings to share. We’ve rolled everything into a brand new report full of stories, data, and expert perspective and advice to help you tackle the future head-on as the security landscape continues to evolve.
Here we’ve extracted five lessons you’ll find in F-Secure’s “State of Cyber Security 2017” – lessons that can shape and strengthen your approach to your business’s security. And don’t worry, there’s plenty more where these came from.
1. Using default passwords? Just…don’t.
You’re probably used to seeing lists of the most common passwords people use to protect their accounts. But we have something different for you. We’re bringing you inside the mind of an attacker to get a peek at what passwords they try first when trying to break into business systems. So here, we present you…the most common username and password attempts made last year on our Rapid Detection Service’s network of honeypots, or decoy machines that are set up just to lure in the bad guys.

2. First get the basics right, then worry about advanced threats
Our Cyber Security Services teams worked with many companies last year who left core components of their networks unmonitored, leading to breaches they didn’t even notice. Are companies focusing too much on exotic security mechanisms, to the detriment of the core foundations?
Our consultants recommend first mastering information security basics – prevention, detection and response. Begin monitoring your internal network, carefully logging resource accesses on common services, and putting systems in place to look for anomalous traffic patterns.
“Traditional techniques executed well still work,” they say. “If you feel your current monitoring capabilities are up to scratch, then it makes sense to reach for the next level.”
3. Exploit kits are dying…but social engineering is staying for a while
Exploit kits are on the decline. Just take a look at this graph from last year, which tracks the activity of five of the biggest exploit kits. As notoriously risky Adobe Flash continues to be de-emphasized, authors of exploit kits simply have less to work with. Our threat intelligence team predicts no new exploit kits will appear in 2017.
But don’t celebrate just yet…that means attackers will be focusing their efforts on social engineering and spam. So continue to educate your employees in these areas.

4. Vulnerable third parties – a weak link
Our CSS consultants are ever wary of upstream attacks, or targeting a primary target via a third party. They know from their own red teaming gigs that tactics such as imitating a carpet cleaning company will gain them access to many physical locations. Such tactics are used by hostile adversaries, and we saw examples of these sort of attacks in 2016.
This is a cautionary tale for businesses. Do you know the level of security your external contractors, partners and suppliers are protected by? What kind of information are you sharing with them? Are your systems integrated with theirs? When bringing in a partner, being mindful of their security practices is important in protecting your business. You’ll find some good advice in the report about how to approach this topic we like to call upstream threats.
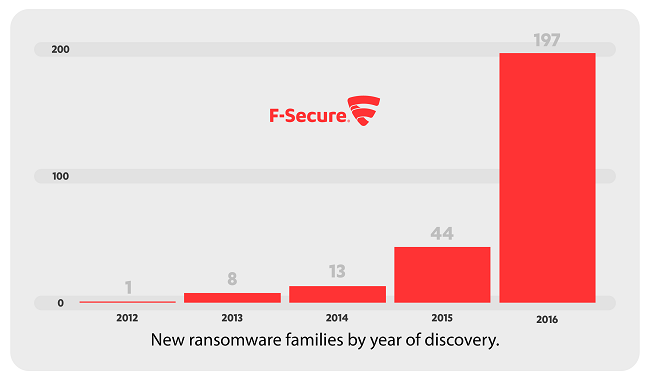
5. Ransomware. Enough said.
Nope, it’s not going anywhere, and the graph below says it all. If you haven’t already, 2017 is a great time to get your business prepared for a ransomware attack by starting to take regular backups. (Check out this quick guide if you’d like to get up to speed on the basics of ransomware.) Hopefully it will never happen, but if it does you’ll be in a much better position to deal with it.
Want more? Check out the full report, “State of Cyber Security 2017” for more hot topics and stories from the trenches:
- Mirai, DDos and IoT
- Vulnerability data – what we’re seeing from our scanning solution
- Cyber sleuthing to find the bad guys
- The business of DNS hijacking
- PC and Android malware trends
…and so much more.
Categories