Attack Landscape H2 2019: An unprecedented year for cyber attacks
The last year of the decade set a new standard for cyber attacks. F-Secure’s Attack Landscape H2 2019 notes that while the impact of sophisticated ransomware attacks continues to be devastating, most of the billions of attacks we see target devices that don’t have keyboards.
In the first half of 2019, we saw a jump in attack traffic to our global network of honeypots from millions of hits to 2.9 billion. In the second half of the year, this pace continued with 2.8 billion hits to our servers. DDoS attacks drove this deluge, accounting for two thirds of the traffic. Honeypot traffic was driven by action aimed at the SMB and Telnet protocols. This shows persistent attacker interest in the Eternal Blue vulnerability, which was first made public in 2017.

Attacks on the IoT still dominate
The explosion in attack traffic tracks the explosion of the Internet of Things (IoT) and threats that target IoT devices. As a result, most of the malicious traffic we see today is generated by Linux-based malware like Mirai.
Brute forcing factory default usernames and passwords of IoT devices continues to be an popular way to recruit devices into botnets for DDoS attacks. A great way to see what attackers are interested in is to check out the list of passwords they use in their attacks. From this, we can see that Dahua DVRs and embedded devices such as routers are popular targets.
You were most likely to be infected by spam
Spam continues to be the most popular way to spread malware.
“Spam preys on unsuspecting individuals, making the lack of awareness about threats a weak link for companies, and a lucrative target for malware authors,” says Calvin Gan, Manager at F-Secure’s Tactical Defense Unit. “And with attacks becoming more sophisticated, such as ransomware infections that escalate into data breaches, it’s more important than ever for organizations to improve their cyber defenses in preparation for these attacks.”
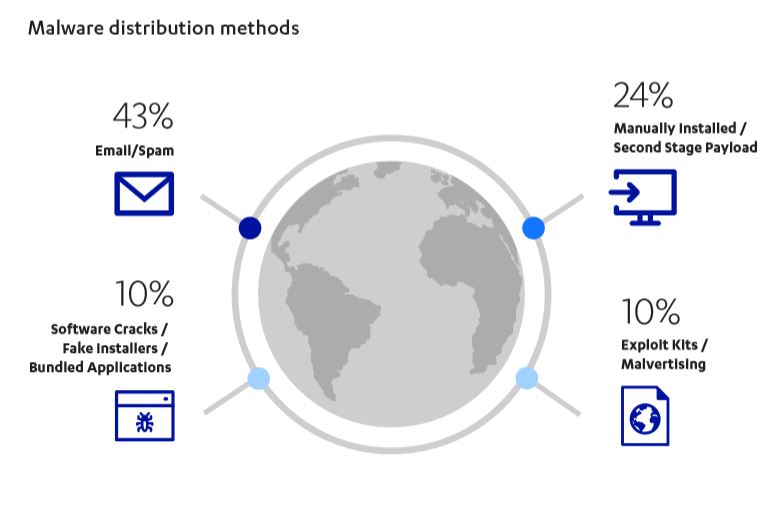
Malicious Word and Excel macro documents acting as downloaders for malicious binaries like Emotet were also common throughout the year.
Who is attacking who?
One of the most fascinating things about our Attack Landscape reports is the numbers that show the source countries where attacks are being launched from and where they are being targeted by destination. The numbers capture mostly criminal not nation-state activity and should be taken with a grain of salt due to purposeful obfuscation. Yet many countries show up on these lists again and again.
Ukraine was the top attack destination, followed by China, Austria and the US. The top aggressors hitting the Ukraine were the United States, the Ukraine itself, and Russia. In the number two spot, the top countries hitting China were China itself, the United States and France, while Austria was hit by China, Russia and the United States. Attacks hitting the United States came from primarily the US, followed by Russia and China.
Ransomware’s evolution and more
In this report, you’ll learn that while ransomware families have declined in numbers, the damage and impact inflicted by these families can be devastating. Find out which ransomware delivery methods are most common. See when ransomware spiked. And learn more details about where cyber attack traffic is targeted.
Our Attack Landscape H2 2019 report takes a look back at the last six months, the last year and the last decade in malware. Get it now.
Get the reportCategories